As technical systems become more connected, OT (Operational Technology) networks face increased risks of cyberattacks. These systems require specialized attention, as traditional IT approaches don't apply.
Cyber Security - Identifying and addressing risks and vulnerabilities in technical networks and systems.

Investing in cybersecurity is essential for businesses.
It ensures both secure operations and the ability to innovate.
The OT environment is a crucial part of it.
Our solution: OT Cyber Security Assessments
We help businesses enhance security with OT Cyber Security Assessments, creating strategies that fit both technical systems and the IT environment.
Our approach manages all physical and digital risks related to building automation, control systems, IoT, and interfaces.
As experts bridging IT, operations, and management, we optimize systems, review network architectures, and plan security improvements, including penetration testing, to protect your infrastructure.
Our approach manages all physical and digital risks related to building automation, control systems, IoT, and interfaces.
As experts bridging IT, operations, and management, we optimize systems, review network architectures, and plan security improvements, including penetration testing, to protect your infrastructure.
Services
Basic Assessment*
- Assessment with checklist
- Report with recommendations
- Report with recommendations
Extended Assessment*
- Assessment with checklist
- Extended subject areas
- Report with recommendations
- Extended subject areas
- Report with recommendations
Optimizations*
- Step-by-step implementation of recommendations and measures
- Coordination of ICT and other partners
- Coordination of ICT and other partners
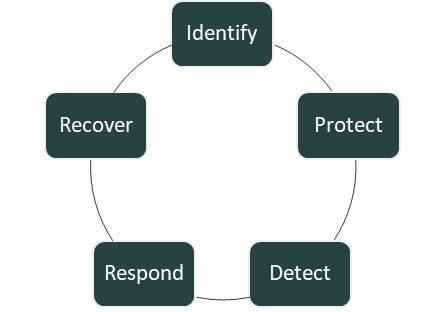
* Assessments based on ICT minimal standard and NIST Cyber Security Framework
“Cybersecurity in technical environments, particularly in buildings, is often underestimated. There are numerous interfaces, remote access points, physically unsecured network components, and software and hardware that are often decades old. Without appropriate measures, it’s only a matter of time before these entry points are exploited in an attack.“
Adrian Staudenmaier
Digital Building Leader
Digital Building Leader
“Cybersecurity in technical environments, particularly in buildings, is often underestimated. There are numerous interfaces, remote access points, physically unsecured network components, and software and hardware that are often decades old. Without appropriate measures, it’s only a matter of time before these entry points are exploited in an attack".
Adrian Staudenmaier
Digital Building Leader
Digital Building Leader